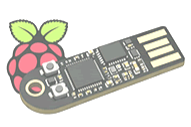
Token2 Pico - RP2350-Based FIDO2 Security Keys
FIDO2 Key Built on RP2350
The RP2350 is an affordable, powerful dual-core microcontroller from Raspberry Pi. We've built a FIDO2 security key on it—delivering passwordless, phishing-resistant authentication without expensive secure chips. It's not military-grade secure, but secure enough for everyday use, and the big advantage is it's cheap to manufacture, easy to assemble, and simple to program and update.
Overview
Token2 provides RP2350-based FIDO2 / WebAuthn authentication keys running a hardened, modified pico-fido firmware. These keys are designed primarily for developers and advanced users who need affordable, standards-compliant FIDO2 keys for testing, development, or deployment scenarios.
They provide strong protection against online attacks, such as phishing or credential theft, while being easy to manage using the fido2-manage CLI tool (optionally available with a GUI wrapper). Please note that these keys cannot be managed using the Token2 Companion App.
Why RP2350 + Token2 Firmware
- The RP2350 microcontroller offers more memory and faster cores (ARM Cortex-M33 + RISC-V), enabling modern cryptographic operations and multiple FIDO2 credentials.
- Token2 uses a modified pico-fido firmware with PIN complexity enforcement, stability improvements, and full FIDO2 compliance.
- By leveraging commodity hardware, Token2 delivers keys at low cost while maintaining full FIDO2 standard support.
Key Features
- Full FIDO2 / WebAuthn support (CTAP 1 & 2, resident credentials, PIN-based user verification).
- User-presence via physical button.
- Support for multiple elliptic curves and standard cryptographic algorithms.
- Manageable via the
fido2-managetool (credential listing, PIN reset, key management) or standard tools like Windows Control Panel and Chromium Security Keys management. - Not compatible with the Token2 Companion App.
Attestation and System Compatibility
These RP2350-based keys do not provide attestation, because Token2 cannot export the private attestation key required by FIDO Alliance. As a result:
- Some services requiring attestation (e.g., AGOV, ID-Austria) are not compatible.
- Other systems may require minor configuration changes (e.g., for Entra ID, the “enforce attestation” setting must be disabled).
Security Considerations
Recommended Usage
- Best suited for developers and advanced users needing affordable FIDO2 keys for testing, development, or deployment.
- Ideal for everyday FIDO2 authentication, backups, or mass deployment in low-risk physical environments.
- Not recommended for high-security scenarios where protection against advanced physical attacks is required.
Pre-Installed Yet Upgradeable Firmware
The Token2 Pico keys are shipped with pre-installed firmware (pico-fido with PIN complexity enforcement) and are fully functional out of the box. However, the firmware is not locked, which means advanced users can replace it with alternative firmware if required. To do so, the device can be put into bootloader mode using the dedicated boot button on the key, as described below, allowing firmware upload via the supported flashing tools. This provides flexibility for development, customization, or recovery scenarios without permanently restricting the device.BOOT Button
By default, the BOOT button on the RP2350 is used for other system functions. In our FIDO2 implementation, this button serves as the user action interface—commonly referred to as the touch button (systems may label it differently, such as “golden area”). Pressing this button allows the user to confirm presence or interact with the FIDO2 functionality.
 When the device is connected to a host system while the BOOT button is held, it starts in a dedicated bootloader (firmware upload) mode instead of normal operating mode. In this state, the key presents itself to the host as a USB mass storage device, allowing firmware files to be transferred using standard file copy operations.
When the device is connected to a host system while the BOOT button is held, it starts in a dedicated bootloader (firmware upload) mode instead of normal operating mode. In this state, the key presents itself to the host as a USB mass storage device, allowing firmware files to be transferred using standard file copy operations.This mechanism enables straightforward firmware updates, recovery, or replacement without requiring proprietary tools. Once the firmware file is copied, the device can be rebooted to apply the update and return to normal operation.
For security or deployment reasons, this behavior can be disabled via device configuration. However, it is important to note that disabling bootloader access will make the key non-upgradable, as it will no longer be possible to enter firmware upload mode using the BOOT button. Re-enabling firmware updates after this point will not be possible without specialized hardware or factory intervention.
LED Behavior for Mounted and Button Modes
Note: This is the default behavior of the pre-installed firmware. You can modify these timings yourself when compiling by editing the led.h file in the SDK.. The LED blinking patterns have been modified from the original default values in the pico-fido project.
-
MODE_MOUNTED
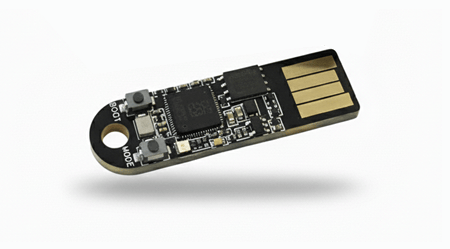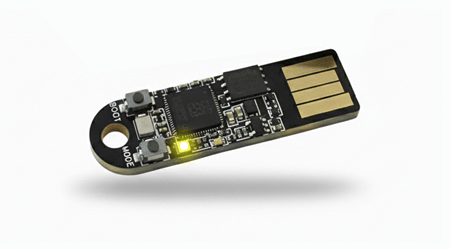
When the device is plugged in and ready for use, the LED will blink once every 3 seconds.
This slow blink indicates that the authenticator is idle but properly mounted and connected. -
MODE_BUTTON
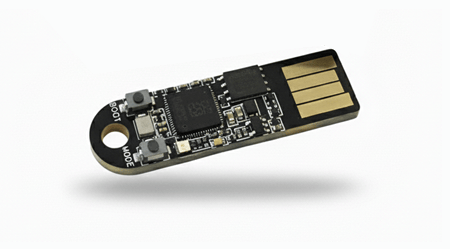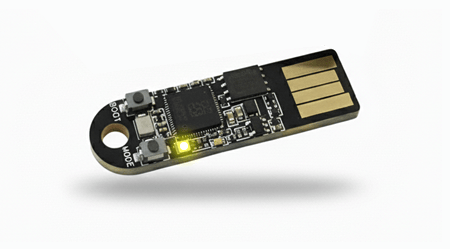
When user interaction is required via the BOOT button (labeled on the board), the LED will blink every 50 ms.
A fast blink indicates that the user should press the button to continue an operation, for example, to confirm their presence after entering a PIN.
Comparison: Token2 RP2350 Keys vs Secure-Element FIDO2 Keys
| Feature | Token2 RP2350 Keys | Token2 Secure-Element Keys |
|---|---|---|
| Price | Very low / budget-friendly | Higher |
| Protocol Support | FIDO2/WebAuthn ony by default with the option to upload other firmware such as PGP. |
FIDO2 / WebAuthn + additional protocols (PIV, OpenPGP, etc.) |
| Firmware Visibility | Open-source (modified pico-fido) | Open source (Java Applet-based) |
| Resistance to Online Attacks | Strong | Strong |
| Resistance to Physical Attacks | Moderate (RP2350 vulnerabilities) | High (secure-element, tamper-resistant) |
| Key Management | fido2-manage |
Vendor apps or CLI |
| Attestation | Not provided | Provided (certified by FIDO Alliance) |
| Mass Deployment | ✅ | ✅ (but higher cost) |
Summary
Token2 RP2350-based FIDO2 keys provide a cost-effective, standards-compliant solution for developers and advanced users who want hardware-backed authentication. They protect fully against online attacks, are manageable via the fido2-manage tool, and are ideal for large-scale deployment or backup keys.
Users should be aware that these keys do not provide attestation and have moderate resistance to physical attacks. They are not a replacement for secure-element keys in high-security environments.
Materials & Open Hardware / Software

As an open hardware and open software initiative, the Token2 RP2350-based FIDO2 security keys are designed with full transparency and openness in mind. Every aspect of the device—from the choice of microcontroller and security components to the firmware and software stack—is made accessible and documented. This level of openness ensures that developers, security researchers, and hardware enthusiasts can fully understand how the key is built, verify its security, and even reproduce or modify the hardware if they wish. By providing complete visibility into the materials, components, and design decisions, we aim to foster a community of trust, collaboration, and innovation around secure authentication hardware. The repository includes all the resources needed to understand, reproduce, and modify the hardware design. Specifically, it contains the schematics (SCH), printed circuit board (PCB) layouts, and a complete bill of materials (BOM) listing all components used. The PCB files are provided in standard Gerber format, which can be used directly for manufacturing.
RP2350-USB Open-Hardware Project - Bill of Materials (BOM)
| ID | Material Name | Specification | Footprint | Designator(s) | Tolerance | Qty |
|---|---|---|---|---|---|---|
| 1 | Black PCB RP2350-USB-V0.6, double-sided, 2.4mm (+0.15/-0.05), gold finger 5U + ENIG | RP2350-USB-V0.6 | Thickness 2.4mm | — | +0.15/-0.05 | 1 |
| 2 | Chip Capacitor 12pF 50V NPO | 12pF | 0402 | C10, C11 | ±5% | 2 |
| 3 | Chip Capacitor 0.1uF 10V X5R | 0.1uF | 0402 | C1–C9 | ±10% | 9 |
| 4 | Chip Capacitor 4.7uF 10V X5R | 4.7uF | 0402 | C14, C15 | ±10% | 2 |
| 5 | Chip Capacitor 10uF 10V X5R | 10uF | 0603 | C12, C13 | ±20% | 2 |
| 6 | Chip Resistor 27Ω 1/16W | 27R, 1% | 0402 | R6, R7 | ±1% | 2 |
| 7 | Chip Resistor 1KΩ 1/16W | 1K, 1% | 0402 | R5, R8 | ±1% | 2 |
| 8 | Chip Resistor 2.7KΩ 1/16W | 2.7K | 0402 | R10 | ±5% | 1 |
| 9 | Chip Resistor 10KΩ 1/16W | 10K, 1% | 0402 | R9 | ±1% | 1 |
| 10 | Chip Resistor 200Ω 1/16W | 200R | 0402 | R4 | ±5% | 1 |
| 11 | White LED 0603 | White | LED-0603 | LED2 | — | 1 |
| 12 | LED YY-0807BRGK03-07-FI | YY-0807BRGK03-07-FI | LED-0807 | LED1 | — | 1 |
| 13 | Power Inductor 3.3uH 2.3A | 3.3uH | 0806 | L1 | ±20% | 1 |
| 14 | ESD Diode PESDMC2FD5VB | PESDMC2FD5VB | DFN1006 | T2, T3 | — | 2 |
| 15 | ESD Diode ESD54371SN | ESD54371SN | DFN1006 | T1, T4–T8 | — | 6 |
| 16 | MCU RP2350A | RP2350A0A4 | QFN60-0.4-GND | U2 | — | 1 |
| 17 | SPI Flash W25Q128JVPIQ | W25Q128JVPIQ | DFN8 5×6 | U3 | — | 1 |
| 18 | LDO 3.3V LN1152B332MR | LN1152B332MR | SOT-25 | U4 | — | 1 |
| 19 | Tactile Switch 180g force | 180g | 4×3×2.5 | S1, S2 | — | 2 |
| 20 | Crystal 12MHz 3.2×2.5mm 10ppm 10pF | 12MHz / 10ppm / 10pF | 3225 | X1 | — | 1 |
view on GitHub All software used is open-source and can be freely reviewed, modified, or compiled by developers.
This ensures full transparency and allows the community to contribute improvements or verify security.
Subscribe to our mailing list
Want to keep up-to-date with the latest Token2 news, projects and events? Join our mailing list!