Security of the TOTP hardware token secret keys (seeds)
We have been receiving questions regarding the security of the shared secret key hashes (seeds) for our hardware tokens. On this page, we explain how this data is secured, operated, stored, and destroyed.
The seeds are randomly generated and securely sent to the factory (we use GPG encryption).
We store them on our servers for a limited period, deleting them after they are transferred to end-users. The servers storing the secret seeds can only be accessed from our office network, and access is protected with two-factor authentication. Our production servers are located exclusively in Switzerland.
Following the recommendation of RFC6238 R7, the permanent storage of seeds is carried out at UBS Safe, which is essentially our e-banking account-attached storage and boasts the highest level of security (MFA protected, PCI-DSS compliant, etc.). Compliance with this recommendation, along with all other RFC6238 recommendations, was assessed by an external company (CertX AG, the first Swiss accredited certification body for product certification in the scope of industrial cybersecurity and functional safety) and confirmed as part of the Independent Compliance Check report. The report is available here.
When transferring keys to end users, we strongly recommend using PGP or GPG encryption to transfer secret keys for all types of tokens. PGP and GPG are popular solutions for encrypting, decrypting, signing, and verifying messages and files, often used in email communications and package repository identity verification. If you are new to PGP, we recommend checking out PGPTool
Furthermore, in this context, it's worth mentioning the following:
- All our employees use multi-factor authentication wherever possible. In addition to corporate email accounts, personal email and social network accounts are also protected with 2FA.
- TOKEN2 began as a research project with the University of Geneva. The core operations team members hold M.Sc./Ph.D. degrees in Information Security.
If you have concerns, there is an option to set the seeds yourself, giving you full control and ensuring no one else has access to your seeds. This option is only available with our programmable tokens. The procedures are explained below.
Hardware Token Provisioning with Full Seed Control
TOKEN2 has developed a simple HTML5 application ("Token2 TOTP Toolset") that can be run locally without accessing any external resources on the Internet, including QR image generation. This application is designed to generate random seeds and produce a CSV file ready to be imported into Azure MFA. The source code for the application is available on GitHub.
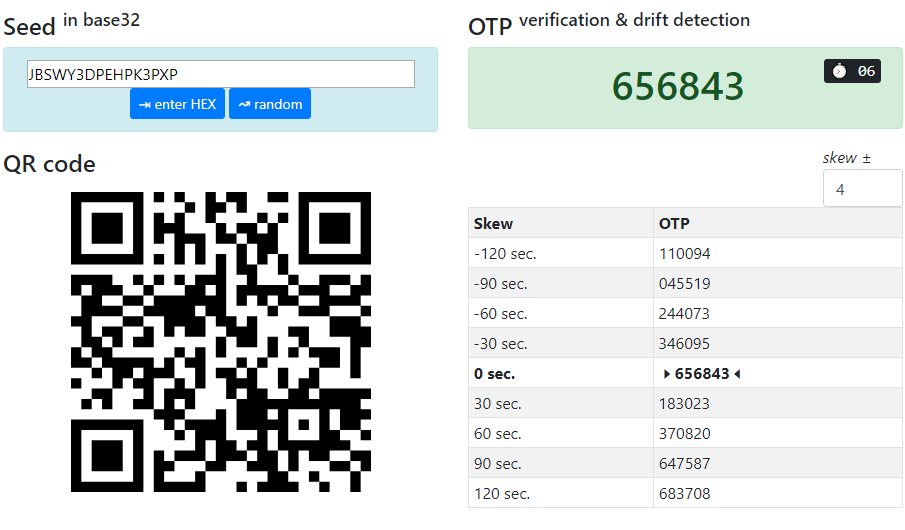
The provisioning process is as follows:
- Download and launch Token2 TOTP Toolset - local. You may want to run this app on a computer that is fully offline (or firewalled) to ensure no information is being transferred to third parties
- Install the Token2 Burner App on an Android device with NFC. After installation, you can set the device to flight mode with Bluetooth, Wi-Fi, and Cellular data off to ensure no data is transferred outside.
- Generate a random seed using the Token2 TOTP Toolset.
- After generating the seed, burn it using the Burner App
- Verify the OTP shown on the device with the OTP value shown on the TOTP Toolset
- Enter the serial number of your token and the username in UPN format into the relevant fields on the TOTP Toolset and click on " ⇲ append to CSV" button
- Repeat steps 3 to 6 for every token you are provisioning
- Click on "save as file" button and save your MFA CSV file
- Import the CSV into Azure MFA
- Your tokens are now ready to be activated for users
You can also download and use the python version of the burner/USB config tools - this will give you full transparency as you will have access to the source code of the provisioning tools.
Subscribe to our mailing list
Want to keep up-to-date with the latest Token2 news, projects and events? Join our mailing list!
