TOTPRadius LDAP Configuration
LDAP Proxy
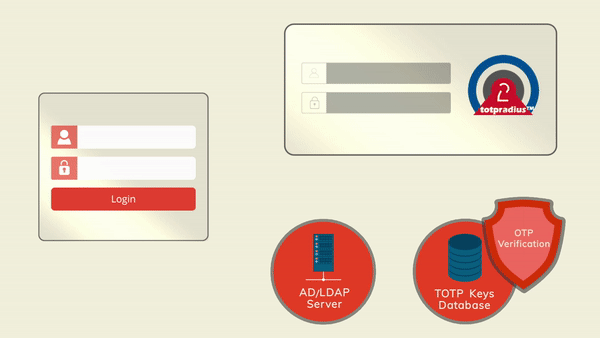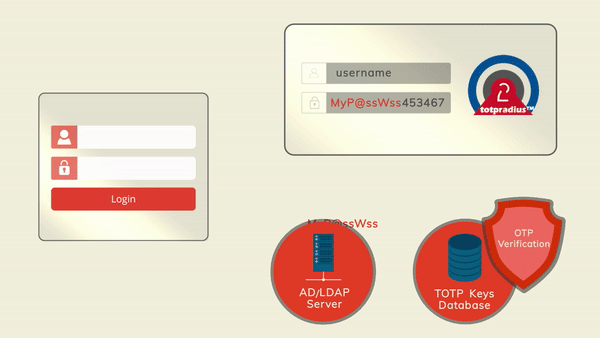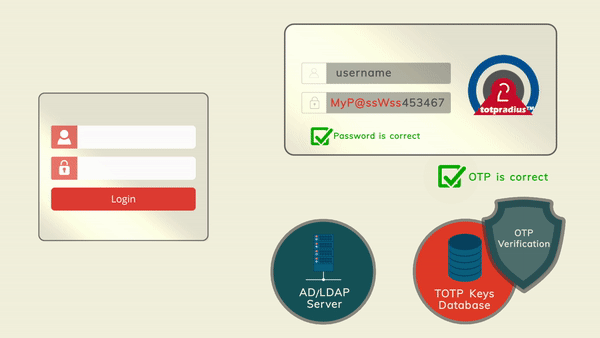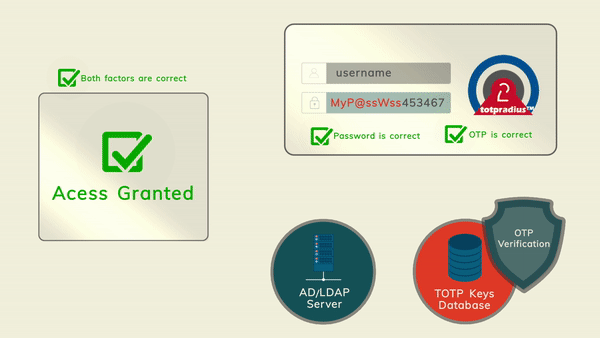
The principle behind it is that users will provide their AD or LDAP password together with the one-time passwords in the password field. TOTPRadius will then parse the password, split it into two parts and authenticate the OTP and if correct will send the AD/LDAP password part further to the AD/LDAP server configuration.
The order of authentication is exactly as stated above, OTP is checked first and AD after OTP is confirmed correct; this is done in order to prevent account lockouts during brute force attacks. Enabling LDAP Proxy on your TOTPRadius appliance allows implementing two-factor authentication for systems that do not natively support it, such as Cisco Meraki VPN, Cisco WLC and many others.
samAccountName attribute. If the UPN is used, its user portion must match the samAccountName.
Configuring LDAP Proxy
LDAP Feature of TOTPRadius can be enabled on the "General settings" page. There are following LDAP related settings:
► LDAP (Enable/Disable) - Enables LDAP verification. This parameter is to be used for systems not supporting 2FA natively. If enabled the system will expect the OTP to be sent together with LDAP password. This setting controls authentication only, not enrollment.
► LDAP server - IP or FQDN of the LDAP server; if you need to specify multiple servers for redundancy, full URIs separated by space must be used. Example "ldap://192.168.200.208 ldap://192.168.200.209" or "ldaps://ADDC01.domain.local ldaps://ADDC02.domain.local " .
Starting from version 0.2.5 LDAPS is also supported, use ldaps:// protocol in the server address . Using LDAPS is possible with FQDN only - make sure you add the CA certificates used by your LDAPS server.
► LDAP username format - Username format. UPN suffix or leading domain name. %username% will be replaced by the actual username. Examples: %username%@domain.local or DOMAIN\%username%. This field cannot be left empty.
Enrollment
These settings are active even if the LDAP proxy feature are not enabled and can be used for self-enrollment using LDAP as the authentication
► Allow ldap enrollment (Enable/Disable) - Allow users to self-enroll their second factor (i.e. generate a QR key) by logging in with LDAP credentials.
► Allow ldap key change (Enable/Disable) - Allow users to re-enroll their second factor (i.e. generate a new QR key) by logging in with LDAP credentials.
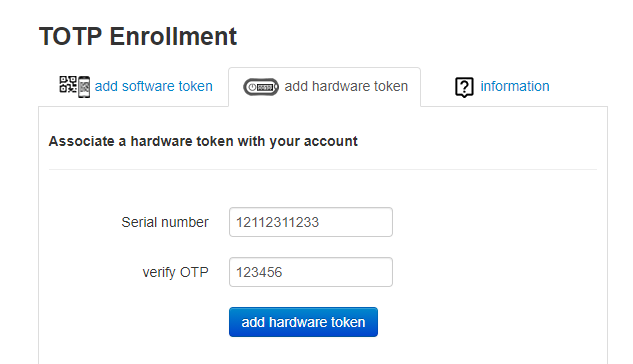 ► Allow ldap web enrollment (Enable/Disable) - Allow users to self-enroll their second factor (i.e. generate a QR key) by logging in with LDAP credentials via the public Web interface (as a part of VPN Portal). For security reasons, this portal allows only the initial enrollment and does not allow re-enrollment. >Starting from version 0.2.5 the web facing enrollment portal also allows associating a hardware token with user's account. The database of the hardware tokens should be added to the admin portal by the system administrator to allow the user to enroll the hardware token.
► Allow ldap web enrollment (Enable/Disable) - Allow users to self-enroll their second factor (i.e. generate a QR key) by logging in with LDAP credentials via the public Web interface (as a part of VPN Portal). For security reasons, this portal allows only the initial enrollment and does not allow re-enrollment. >Starting from version 0.2.5 the web facing enrollment portal also allows associating a hardware token with user's account. The database of the hardware tokens should be added to the admin portal by the system administrator to allow the user to enroll the hardware token.
► Ldap intro text - This text will appear on LDAP web enrollment page. HTML tags are allowed.
About
Installation and configuration
- Installation and initial configuration
- Network configuration
- Migrating from older versions
- LDAP Configuration
- Azure AD Configuration
- Self-service enrollment portal
- Web and LDAPS Certificates
- Syslog configuration
- Single-factor authentication exceptions
- Slave appliance mode
- Dynamic RADIUS Attributes
Integration guides
Blog
21-12-2025
Android, NFC, and the Missing Piece of WebAuthn
 For years, Android users have faced a frustrating limitation—Android does not support CTAP2 over NFC. This means no PIN verification and no discoverable credentials (passkeys) when using NFC, and therefore limited to simple U2F-style flows without user verification. That said, there finally seems to be a solution.
For years, Android users have faced a frustrating limitation—Android does not support CTAP2 over NFC. This means no PIN verification and no discoverable credentials (passkeys) when using NFC, and therefore limited to simple U2F-style flows without user verification. That said, there finally seems to be a solution.
19-12-2025
Streamline Token2 Classic Tokens in Okta
 Token2 classic hardware tokens provide phishing-resistant multi-factor authentication for your Okta environment. Our updated integration guide shows you how to deploy them using Okta's Custom OTP authenticator method.
Token2 classic hardware tokens provide phishing-resistant multi-factor authentication for your Okta environment. Our updated integration guide shows you how to deploy them using Okta's Custom OTP authenticator method.
09-12-2025
Framework ExpansionCard Enclosure for Token2 Keys
 Framework laptops are all about modularity. The Framework ExpansionCard 3D-printable enclosure for Token2 PIN+ Type-C keys brings FIDO2 security directly into your device.
Framework laptops are all about modularity. The Framework ExpansionCard 3D-printable enclosure for Token2 PIN+ Type-C keys brings FIDO2 security directly into your device.
