Hardware tokens for two-factor authentication with FortiGate
 Two-factor authentication with FortiGate can be implemented using several different methods (SMS, Email etc.) with OTP based 2FA being the most secure one. 2FA can be implemented natively with FortiToken, a disconnected one-time password (OTP) generator. It is a small physical device with a button that when pressed displays a six-digit authentication code or a mobile app that uses a proprietary algorithm for the enrollment process. FortiToken is a component of Fortinet infrastructure that requires an additional license (even with the mobile app version), which some customers find quite expensive.
Two-factor authentication with FortiGate can be implemented using several different methods (SMS, Email etc.) with OTP based 2FA being the most secure one. 2FA can be implemented natively with FortiToken, a disconnected one-time password (OTP) generator. It is a small physical device with a button that when pressed displays a six-digit authentication code or a mobile app that uses a proprietary algorithm for the enrollment process. FortiToken is a component of Fortinet infrastructure that requires an additional license (even with the mobile app version), which some customers find quite expensive.
Fortunately, Fortinet allows using external RADIUS servers as the authentication source and this will allow implementing two-factor authentication using Token2 TOTPRadius appliance as a more cost-effective alternative to the standard method.
In this guide, we will show how to configure a Fortinet gateway to work with TOTPRadius in LDAP proxy mode. The authentication will use the standard login forms (username+password only) and the password field is expected to have the LDAP password followed by 6 digit OTP as a single string. For simplicity, this guide will show configuring accounts with administrative access.
About LDAP Proxy
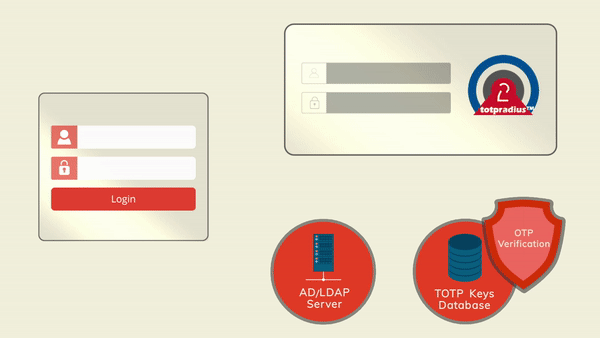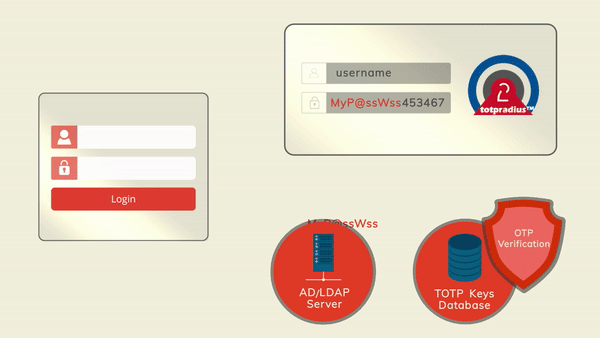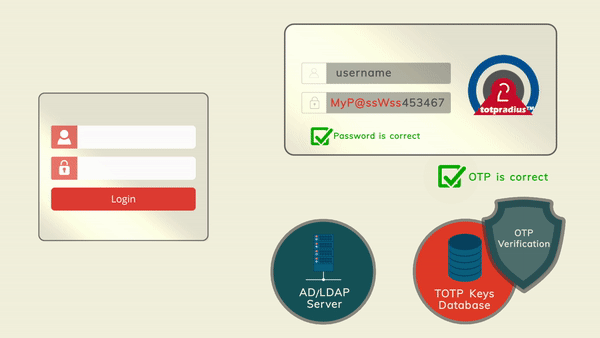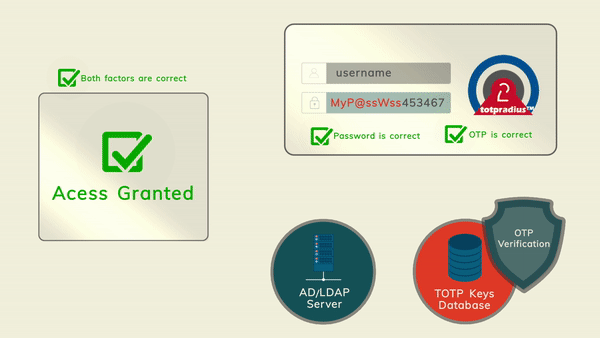
The setup described in this guide is based on the following components:
- Fortinet gateway deployed as a virtual appliance on Vmware ESXi (FortiGate VM64) and full admin access to the gateway
- Token2 TOTPRadius v2.3 with built-in free 5 users license
- A mobile application (such as Google Authenticator) and/or a classic or a programmable Token2 TOTP hardware token used as the second factor
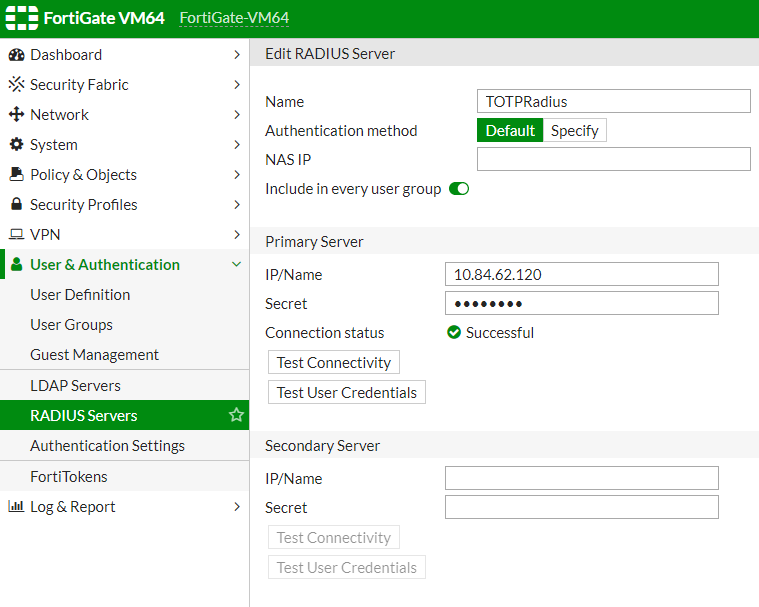
Step 1. Create a new RADIUS server entry and assign to User group
Navigate to User & Authentication -> RADIUS Servers . Click on the '+ Create New' button and fill the information below:
Name: the name of the appliance (we will use 'TOTPRadius' for this guide as an example)
NAS IP: leave empty
IP/Name: the IP address of your TOTPRadius appliance
Secret: RADIUS secret of your TOTPRadius appliance (configured on the 'General settings' page in the admin panel of TOTPRadius)
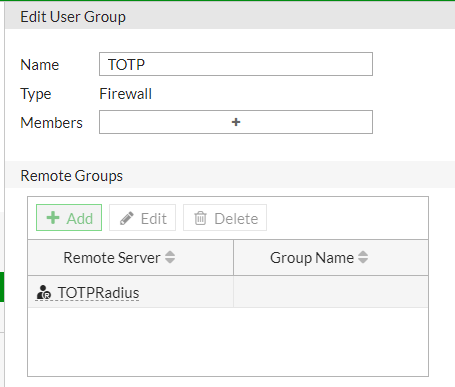
Navigate to User & Authentication -> User Groups and click on the '+ Create New' button. Provide the following information:
- Name: Name of the user group allowed to use TOTPRadius authentication, in our example, we use "TOTP" as the name of the group
- Type: choose 'Firewall'
- Remote Groups: click on Add, then select 'TOTPRadius' from the Remote Server list
- Click 'OK' to complete the process
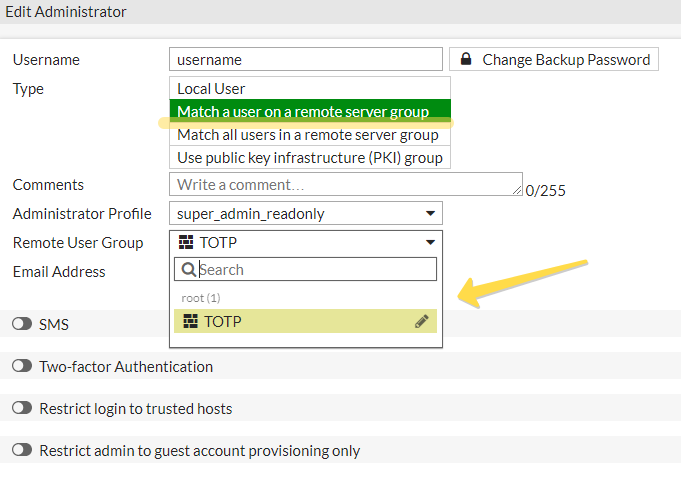
Step 2. Enable administrative access for TOTPRadius hosted users
Navigate to Security -> Administrators, then click on the '+ Create New -> Administrator' button to prepare the account.
Fill the following information:
- Username: same as your LDAP username
- Type: "Match a user on a remote server group"
- Set a backup password and confirm it (this password may be used as a fallback mechanism if the RADIUS server is unreachable)
- Select Administrator Profile, for example, super_admin
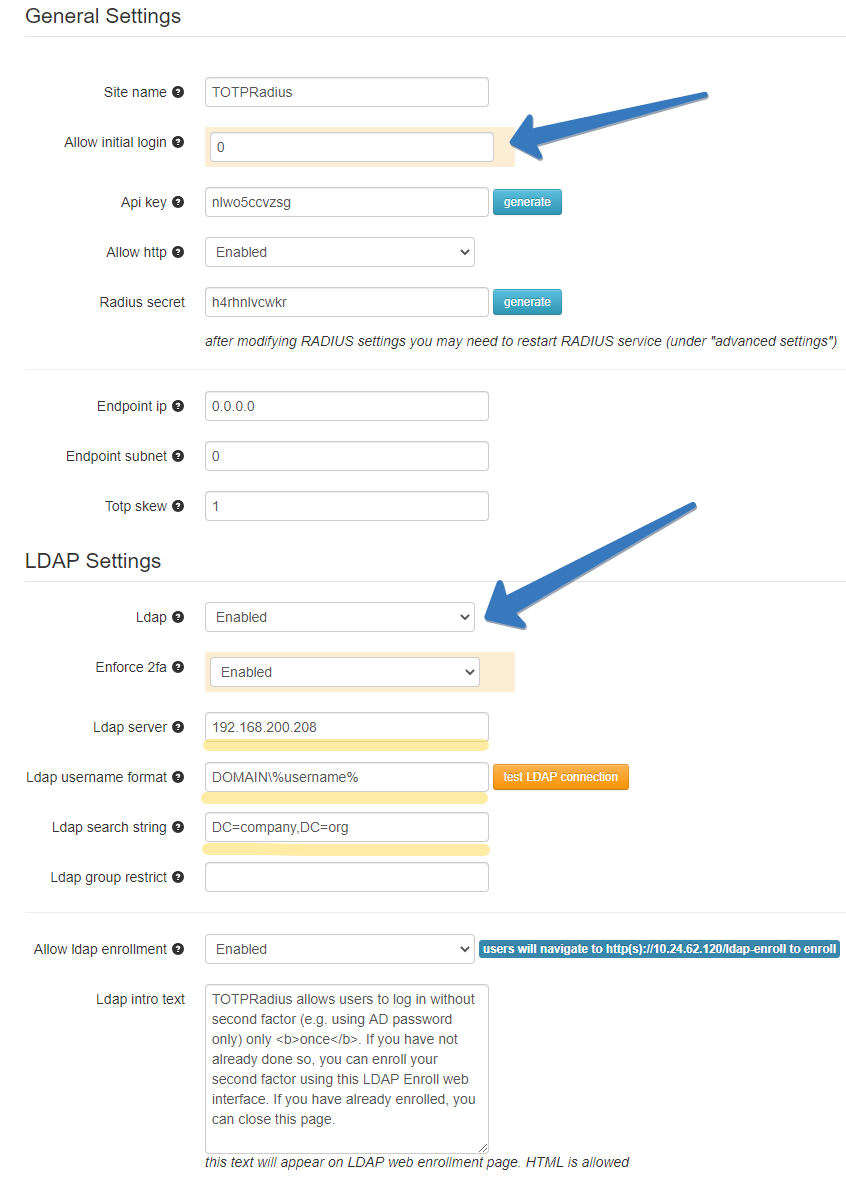
Step 3. Configure TOTPRadius in LDAP Proxy mode
- Set 'Allow initial login' to 0
- in LDAP settings section:
- Set LDAP server (hostname or IP for regular LDAP and ldaps://ip_or_hostname for LDAPS). Separate multiple servers with spaces
- Put your NETBIOS prefix or UPN suffix in the username format field keeping %username% string. I.e. if a user in your AD environment is using [email protected] to log in, the username format field should be set as "%username%@domain.com"
- You also need to define LDAP search string to allow the LDAP connection session to locate the users' OU (i.e. 'ou=users,o=myorgname').
- LDAP Group field should be left empty (this setting is not used by Fortinet integration)
- If you need the user to self-enrol the second factor, enable "Allow LDAP Enrollment" option
Step 4. Generate or set the second factor for the user on TOTPRadius appliance
In this step, we will create a second-factor record (TOTP secret) for the username previously created under the FortiGate interface (Step 2).
Login to TOTPRadius admin interface, and click on New User button. This will generate a QR code that should be used to provision the TOTP profile on a mobile authenticator app (Google Authenticator, Microsoft Authenticator, Token2 TOTP+ or any other RFC6238-compliant application). If a hardware token is to be used for this user, click on Edit profile or assign hardware token button and paste the secret key of the hardware token in Token key field in base32 format.
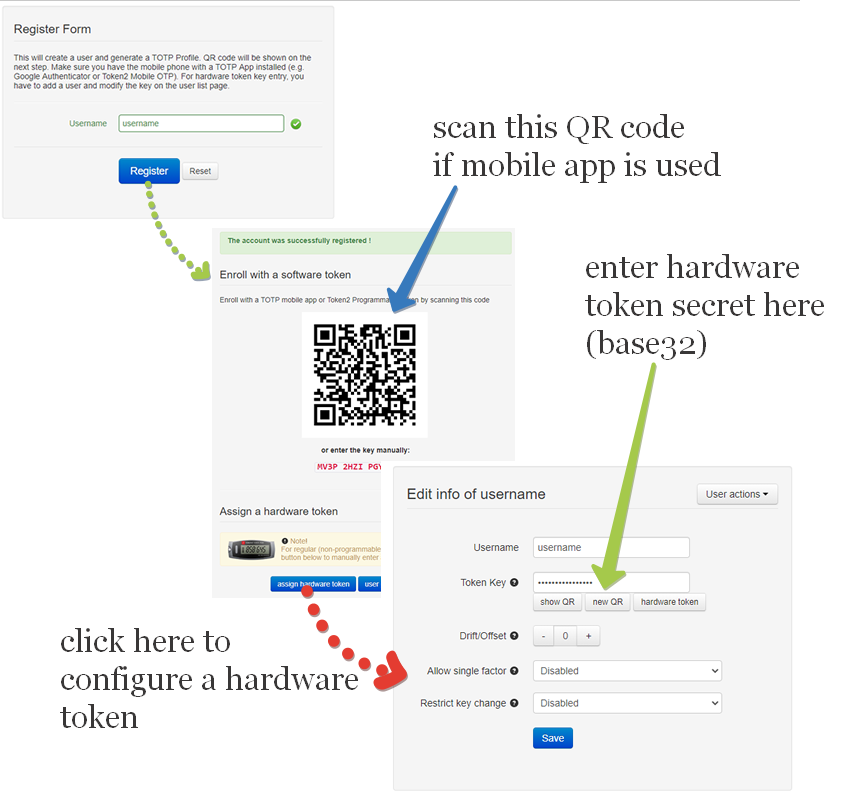
If a programmable hardware token is used, you can burn the secret onto the hardware token by scanning the QR code using one of the NFC Burner apps.
Ready to log in
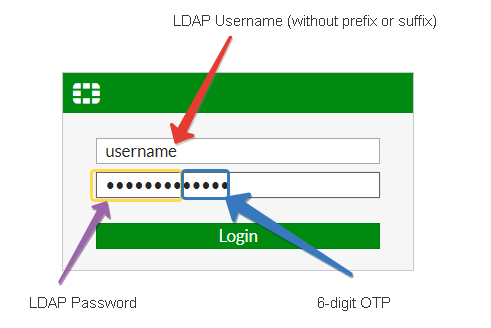
After all 4 steps above are completed successfully and without errors, the user can log in to the Fortinet web interface using his/her username and active directory password and the 6 digit OTP generated by the hardware token or the mobile app.
About
Installation and configuration
- Installation and initial configuration
- Network configuration
- Migrating from older versions
- LDAP Configuration
- Azure AD Configuration
- Self-service enrollment portal
- Web and LDAPS Certificates
- Syslog configuration
- Single-factor authentication exceptions
- Slave appliance mode
- Dynamic RADIUS Attributes
Integration guides
Blog
24-05-2024
Reminder: Our management tools for FIDO2.1 Security Keys are Open Source!
 Just a quick reminder: our FIDO2.1 Manager tool, your go-to solution for managing FIDO2 credentials securely, is fully open source! Both the Windows version, created with PowerShell, and a Linux (C++ and Python) version are available.
Just a quick reminder: our FIDO2.1 Manager tool, your go-to solution for managing FIDO2 credentials securely, is fully open source! Both the Windows version, created with PowerShell, and a Linux (C++ and Python) version are available.
01-05-2024
FIDO2 Security Keys. To PIN or not to PIN?
 Whether to require a PIN when using a FIDO2 security key depends on various factors, including the service provider's authentication settings. This results in situations where some services always prompt for a PIN, while others never do - so we have decided to clarify these aspects.
Whether to require a PIN when using a FIDO2 security key depends on various factors, including the service provider's authentication settings. This results in situations where some services always prompt for a PIN, while others never do - so we have decided to clarify these aspects.
14-04-2024
Adding FIDO2 Security Keys to FINOM accounts

We're pleased to introduce a comprehensive guide on integrating FIDO2 Security Keys into your account with FINOM.
